Dear friends, today we will see how to install kubernetes cluster on CentOS 7 VM step by step. In this tutorial we also know what is kubernetes and how its work? So, let’s start.
What is Kubernetes?
Kubernetes is an open source software or tool which can be used to orchestrate and manage docker containers in cluster environment.
For more details about kubernetes you can also Click Here
In this tutorial I am using three CentOS 7 VM to see how to install kubernetes cluster, where one node will be Master node and another two node will be worker nodes. As you can see below:-
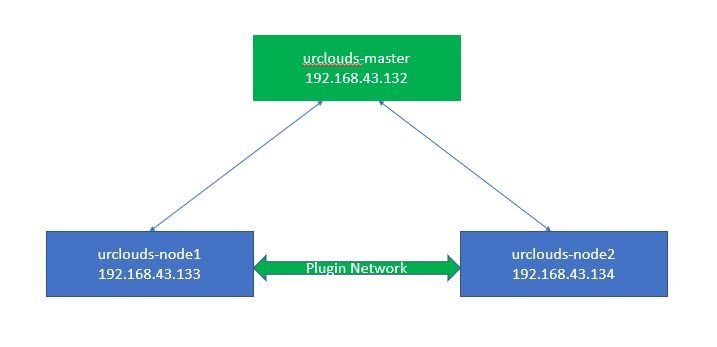
On the Master Node we have to install these components
- API Server: – API sever will provides kubernetes API using Jason / Yaml over http, states of API objects are stored in etcd.
- Scheduler: – Scheduler is a program on master node which performs the scheduling tasks like launching containers in worker nodes based on resource availability.
- Controller Manager: – Controller manager can be used to monitor replication controllers and create pods to maintain desired state.
- Etcd: – It is a Key value pair data base. It stores configuration data of cluster and cluster state.
- Kubectl utility: – Kubectl utility is a command line utility which connects to API Server on port 6443. It’s used by administrators to create pods and services.
On the Worker Nodes we must install these components
- Kubelet: – Kubelet is an agent which runs on every worker node, it connects to docker and takes care of creating, starting, deleting containers.
- Kube-Proxy: – Kube-Proxy routes the traffic to appropriate containers based on IP address and port number of the incoming request. In other words, we can say it is used for port translation.
- Pod: – Pod can be defined as a multi-tier or group of containers that are deployed on a single worker node or docker host.
For more about Kubernetes cluster you can
Let’s start install Kubernetes step by step.
Disable SELinux & Setup firewall rules
First, we have to login on our master node and we need to be setup SELinux and Firewall rules for master node using below commands
[root@localhost ~]# hostnamectl set-hostname urclouds-master [root@localhost ~]# exec bash [root@urclouds-master ~]# setenforce 0 [root@urclouds-master ~]# sed -i --follow-symlinks 's/SELINUX=enforcing/SELINUX=disabled/g' /etc/sysconfig/selinux [root@urclouds-master ~]#
Following rules, we need to set on our master node
[root@urclouds-master ~]# firewall-cmd --permanent --add-port=6443/tcp success [root@urclouds-master ~]# firewall-cmd --permanent --add-port=2379-2380/tcp success [root@urclouds-master ~]# firewall-cmd --permanent --add-port=10250/tcp success [root@urclouds-master ~]# firewall-cmd --permanent --add-port=10251/tcp success [root@urclouds-master ~]# firewall-cmd --permanent --add-port=10252/tcp success [root@urclouds-master ~]# firewall-cmd --permanent --add-port=10255/tcp success [root@urclouds-master ~]# firewall-cmd --reload success [root@urclouds-master ~]# modprobe br_netfilter [root@urclouds-master ~]# echo '1' > /proc/sys/net/bridge/bridge-nf-call-iptables [root@urclouds-master ~]#
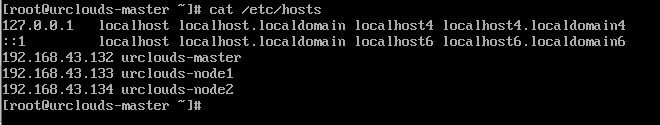
If you don’t have any DNS then you can add entry in /etc/hosts file on Master node and worker node. Like below: –
Configure Kubernetes Repository
We need to be configure repository for downloading kubernetes packages.
[root@urclouds-master ~]# vi /etc/yum.repos.d/kubernetes.repo [root@urclouds-master ~]# cat /etc/yum.repos.d/kubernetes.repo [kubernetes] name=Kubernetes baseurl=https://packages.cloud.google.com/yum/repos/kubernetes-el7-x86_64 enabled=1 gpgcheck=1 repo_gpgcheck=1 gpgkey=https://packages.cloud.google.com/yum/doc/yum-key.gpg https://packages.cloud.google.com/yum/doc/rpm-package-key.gpg [root@urclouds-master ~]#
Install Kubeadm and Docker
Now we can install Kubeadm and Docker package on master node using yum tool like below: –
[root@urclouds-master ~]# yum install kubeadm docker -y Loaded plugins: fastestmirror Loading mirror speeds from cached hostfile base: mirrors.piconets.webwerks.in extras: mirrors.nhanhoa.com updates: mirrors.piconets.webwerks.in kubernetes/signature | 454 B 00:00:00 kubernetes/signature | 1.4 kB 00:00:00 !!! Resolving Dependencies --> Running transaction check ---> Package docker.x86_64 2:1.13.1-103.git7f2769b.el7.centos will be installed --> Processing Dependency: docker-common = 2:1.13.1-103.git7f2769b.el7.centos for package: 2:docker-1.13.1-103.git7f2769b.el7.centos.x86_64 --> Processing Dependency: docker-client = 2:1.13.1-103.git7f2769b.el7.centos for package: 2:docker-1.13.1-103.git7f2769b.el7.centos.x86_64 --> Processing Dependency: subscription-manager-rhsm-certificates for package: 2:docker-1.13.1-103.git7f2769b.el7.centos.x86_64 --> Processing Dependency: libseccomp.so.2()(64bit) for package: 2:docker-1.13.1-103.git7f2769b.el7.centos.x86_64 ---> Package kubeadm.x86_64 0:1.16.3-0 will be installed --> Processing Dependency: kubernetes-cni >= 0.7.5 for package: kubeadm-1.16.3-0.x86_64 --> Processing Dependency: kubelet >= 1.13.0 for package: kubeadm-1.16.3-0.x86_64 --> Processing Dependency: kubectl >= 1.13.0 for package: kubeadm-1.16.3-0.x86_64 --> Processing Dependency: cri-tools >= 1.13.0 for package: kubeadm-1.16.3-0.x86_64 --> Running transaction check ---> Package cri-tools.x86_64 0:1.13.0-0 will be installed ---> Package docker-client.x86_64 2:1.13.1-103.git7f2769b.el7.centos will be installed ---> Package docker-common.x86_64 2:1.13.1-103.git7f2769b.el7.centos will be installed --> Processing Dependency: skopeo-containers >= 1:0.1.26-2 for package: 2:docker-common-1.13.1-103.git7f2769b.el7.centos.x86_64 --> Processing Dependency: oci-umount >= 2:2.3.3-3 for package: 2:docker-common-1.13.1-103.git7f2769b.el7.centos.x86_64 --> Processing Dependency: oci-systemd-hook >= 1:0.1.4-9 for package: 2:docker-common-1.13.1-103.git7f2769b.el7.centos.x86_64 --> Processing Dependency: oci-register-machine >= 1:0-5.13 for package: 2:docker-common-1.13.1-103.git7f2769b.el7.centos.x86_64 --> Processing Dependency: container-storage-setup >= 0.9.0-1 for package: 2:docker-common-1.13.1-103.git7f2769b.el7.centos.x86_64 --> Processing Dependency: container-selinux >= 2:2.51-1 for package: 2:docker-common-1.13.1-103.git7f2769b.el7.centos.x86_64 --> Processing Dependency: atomic-registries for package: 2:docker-common-1.13.1-103.git7f2769b.el7.centos.x86_64 ---> Package kubectl.x86_64 0:1.16.3-0 will be installed ---> Package kubelet.x86_64 0:1.16.3-0 will be installed --> Processing Dependency: socat for package: kubelet-1.16.3-0.x86_64 --> Processing Dependency: conntrack for package: kubelet-1.16.3-0.x86_64 ---> Package kubernetes-cni.x86_64 0:0.7.5-0 will be installed ---> Package libseccomp.x86_64 0:2.3.1-3.el7 will be installed ---> Package subscription-manager-rhsm-certificates.x86_64 0:1.24.13-3.el7.centos will be installed --> Running transaction check ---> Package atomic-registries.x86_64 1:1.22.1-29.gitb507039.el7 will be installed --> Processing Dependency: python-yaml for package: 1:atomic-registries-1.22.1-29.gitb507039.el7.x86_64 --> Processing Dependency: python-setuptools for package: 1:atomic-registries-1.22.1-29.gitb507039.el7.x86_64 --> Processing Dependency: python-pytoml for package: 1:atomic-registries-1.22.1-29.gitb507039.el7.x86_64 ---> Package conntrack-tools.x86_64 0:1.4.4-5.el7_7.2 will be installed --> Processing Dependency: libnetfilter_cttimeout.so.1(LIBNETFILTER_CTTIMEOUT_1.1)(64bit) for package: conntrack-tools-1.4.4-5.el7_7.2.x86_64 --> Processing Dependency: libnetfilter_cttimeout.so.1(LIBNETFILTER_CTTIMEOUT_1.0)(64bit) for package: conntrack-tools-1.4.4-5.el7_7.2.x86_64 --> Processing Dependency: libnetfilter_cthelper.so.0(LIBNETFILTER_CTHELPER_1.0)(64bit) for package: conntrack-tools-1.4.4-5.el7_7.2.x86_64 --> Processing Dependency: libnetfilter_queue.so.1()(64bit) for package: conntrack-tools-1.4.4-5.el7_7.2.x86_64 --> Processing Dependency: libnetfilter_cttimeout.so.1()(64bit) for package: conntrack-tools-1.4.4-5.el7_7.2.x86_64 --> Processing Dependency: libnetfilter_cthelper.so.0()(64bit) for package: conntrack-tools-1.4.4-5.el7_7.2.x86_64 ---> Package container-selinux.noarch 2:2.107-3.el7 will be installed --> Processing Dependency: selinux-policy-targeted >= 3.13.1-216.el7 for package: 2:container-selinux-2.107-3.el7.noarch --> Processing Dependency: selinux-policy-base >= 3.13.1-216.el7 for package: 2:container-selinux-2.107-3.el7.noarch --> Processing Dependency: selinux-policy >= 3.13.1-216.el7 for package: 2:container-selinux-2.107-3.el7.noarch --> Processing Dependency: policycoreutils-python for package: 2:container-selinux-2.107-3.el7.noarch ---> Package container-storage-setup.noarch 0:0.11.0-2.git5eaf76c.el7 will be installed ---> Package containers-common.x86_64 1:0.1.37-3.el7.centos will be installed ---> Package oci-register-machine.x86_64 1:0-6.git2b44233.el7 will be installed ---> Package oci-systemd-hook.x86_64 1:0.2.0-1.git05e6923.el7_6 will be installed --> Processing Dependency: libyajl.so.2()(64bit) for package: 1:oci-systemd-hook-0.2.0-1.git05e6923.el7_6.x86_64 ---> Package oci-umount.x86_64 2:2.5-3.el7 will be installed ---> Package socat.x86_64 0:1.7.3.2-2.el7 will be installed --> Running transaction check ---> Package PyYAML.x86_64 0:3.10-11.el7 will be installed --> Processing Dependency: libyaml-0.so.2()(64bit) for package: PyYAML-3.10-11.el7.x86_64 ---> Package libnetfilter_cthelper.x86_64 0:1.0.0-10.el7_7.1 will be installed ---> Package libnetfilter_cttimeout.x86_64 0:1.0.0-6.el7_7.1 will be installed ---> Package libnetfilter_queue.x86_64 0:1.0.2-2.el7_2 will be installed ---> Package policycoreutils-python.x86_64 0:2.5-33.el7 will be installed --> Processing Dependency: policycoreutils = 2.5-33.el7 for package: policycoreutils-python-2.5-33.el7.x86_64 --> Processing Dependency: setools-libs >= 3.3.8-4 for package: policycoreutils-python-2.5-33.el7.x86_64 --> Processing Dependency: libsemanage-python >= 2.5-14 for package: policycoreutils-python-2.5-33.el7.x86_64 --> Processing Dependency: audit-libs-python >= 2.1.3-4 for package: policycoreutils-python-2.5-33.el7.x86_64 --> Processing Dependency: python-IPy for package: policycoreutils-python-2.5-33.el7.x86_64 --> Processing Dependency: libqpol.so.1(VERS_1.4)(64bit) for package: policycoreutils-python-2.5-33.el7.x86_64 --> Processing Dependency: libqpol.so.1(VERS_1.2)(64bit) for package: policycoreutils-python-2.5-33.el7.x86_64 --> Processing Dependency: libcgroup for package: policycoreutils-python-2.5-33.el7.x86_64 --> Processing Dependency: libapol.so.4(VERS_4.0)(64bit) for package: policycoreutils-python-2.5-33.el7.x86_64 --> Processing Dependency: checkpolicy for package: policycoreutils-python-2.5-33.el7.x86_64 --> Processing Dependency: libqpol.so.1()(64bit) for package: policycoreutils-python-2.5-33.el7.x86_64 --> Processing Dependency: libapol.so.4()(64bit) for package: policycoreutils-python-2.5-33.el7.x86_64 ---> Package python-pytoml.noarch 0:0.1.14-1.git7dea353.el7 will be installed ---> Package python-setuptools.noarch 0:0.9.8-7.el7 will be installed --> Processing Dependency: python-backports-ssl_match_hostname for package: python-setuptools-0.9.8-7.el7.noarch ---> Package selinux-policy.noarch 0:3.13.1-192.el7 will be updated ---> Package selinux-policy.noarch 0:3.13.1-252.el7.1 will be an update --> Processing Dependency: libsemanage >= 2.5-13 for package: selinux-policy-3.13.1-252.el7.1.noarch ---> Package selinux-policy-targeted.noarch 0:3.13.1-192.el7 will be updated ---> Package selinux-policy-targeted.noarch 0:3.13.1-252.el7.1 will be an update ---> Package yajl.x86_64 0:2.0.4-4.el7 will be installed --> Running transaction check ---> Package audit-libs-python.x86_64 0:2.8.5-4.el7 will be installed --> Processing Dependency: audit-libs(x86-64) = 2.8.5-4.el7 for package: audit-libs-python-2.8.5-4.el7.x86_64 ---> Package checkpolicy.x86_64 0:2.5-8.el7 will be installed ---> Package libcgroup.x86_64 0:0.41-21.el7 will be installed ---> Package libsemanage.x86_64 0:2.5-11.el7 will be updated ---> Package libsemanage.x86_64 0:2.5-14.el7 will be an update --> Processing Dependency: libsepol >= 2.5-10 for package: libsemanage-2.5-14.el7.x86_64 --> Processing Dependency: libselinux >= 2.5-14 for package: libsemanage-2.5-14.el7.x86_64 ---> Package libsemanage-python.x86_64 0:2.5-14.el7 will be installed ---> Package libyaml.x86_64 0:0.1.4-11.el7_0 will be installed ---> Package policycoreutils.x86_64 0:2.5-22.el7 will be updated ---> Package policycoreutils.x86_64 0:2.5-33.el7 will be an update --> Processing Dependency: libselinux-utils >= 2.5-14 for package: policycoreutils-2.5-33.el7.x86_64 ---> Package python-IPy.noarch 0:0.75-6.el7 will be installed ---> Package python-backports-ssl_match_hostname.noarch 0:3.5.0.1-1.el7 will be installed --> Processing Dependency: python-ipaddress for package: python-backports-ssl_match_hostname-3.5.0.1-1.el7.noarch --> Processing Dependency: python-backports for package: python-backports-ssl_match_hostname-3.5.0.1-1.el7.noarch ---> Package setools-libs.x86_64 0:3.3.8-4.el7 will be installed --> Running transaction check ---> Package audit-libs.x86_64 0:2.8.1-3.el7 will be updated --> Processing Dependency: audit-libs(x86-64) = 2.8.1-3.el7 for package: audit-2.8.1-3.el7.x86_64 ---> Package audit-libs.x86_64 0:2.8.5-4.el7 will be an update ---> Package libselinux.x86_64 0:2.5-12.el7 will be updated --> Processing Dependency: libselinux(x86-64) = 2.5-12.el7 for package: libselinux-python-2.5-12.el7.x86_64 ---> Package libselinux.x86_64 0:2.5-14.1.el7 will be an update ---> Package libselinux-utils.x86_64 0:2.5-12.el7 will be updated ---> Package libselinux-utils.x86_64 0:2.5-14.1.el7 will be an update ---> Package libsepol.x86_64 0:2.5-8.1.el7 will be updated ---> Package libsepol.x86_64 0:2.5-10.el7 will be an update ---> Package python-backports.x86_64 0:1.0-8.el7 will be installed ---> Package python-ipaddress.noarch 0:1.0.16-2.el7 will be installed --> Running transaction check ---> Package audit.x86_64 0:2.8.1-3.el7 will be updated ---> Package audit.x86_64 0:2.8.5-4.el7 will be an update ---> Package libselinux-python.x86_64 0:2.5-12.el7 will be updated ---> Package libselinux-python.x86_64 0:2.5-14.1.el7 will be an update --> Finished Dependency Resolution Dependencies Resolved ======================================================================================================================================================================== Package Arch Version Repository Size Installing: docker x86_64 2:1.13.1-103.git7f2769b.el7.centos extras 18 M kubeadm x86_64 1.16.3-0 kubernetes 9.5 M Installing for dependencies: PyYAML x86_64 3.10-11.el7 base 153 k atomic-registries x86_64 1:1.22.1-29.gitb507039.el7 extras 35 k audit-libs-python x86_64 2.8.5-4.el7 base 76 k checkpolicy x86_64 2.5-8.el7 base 295 k conntrack-tools x86_64 1.4.4-5.el7_7.2 updates 187 k container-selinux noarch 2:2.107-3.el7 extras 39 k container-storage-setup noarch 0.11.0-2.git5eaf76c.el7 extras 35 k containers-common x86_64 1:0.1.37-3.el7.centos extras 21 k cri-tools x86_64 1.13.0-0 kubernetes 5.1 M docker-client x86_64 2:1.13.1-103.git7f2769b.el7.centos extras 3.9 M docker-common x86_64 2:1.13.1-103.git7f2769b.el7.centos extras 97 k kubectl x86_64 1.16.3-0 kubernetes 10 M kubelet x86_64 1.16.3-0 kubernetes 22 M kubernetes-cni x86_64 0.7.5-0 kubernetes 10 M libcgroup x86_64 0.41-21.el7 base 66 k libnetfilter_cthelper x86_64 1.0.0-10.el7_7.1 updates 18 k libnetfilter_cttimeout x86_64 1.0.0-6.el7_7.1 updates 18 k libnetfilter_queue x86_64 1.0.2-2.el7_2 base 23 k libseccomp x86_64 2.3.1-3.el7 base 56 k libsemanage-python x86_64 2.5-14.el7 base 113 k libyaml x86_64 0.1.4-11.el7_0 base 55 k oci-register-machine x86_64 1:0-6.git2b44233.el7 extras 1.1 M oci-systemd-hook x86_64 1:0.2.0-1.git05e6923.el7_6 extras 34 k oci-umount x86_64 2:2.5-3.el7 extras 33 k policycoreutils-python x86_64 2.5-33.el7 base 457 k python-IPy noarch 0.75-6.el7 base 32 k python-backports x86_64 1.0-8.el7 base 5.8 k python-backports-ssl_match_hostname noarch 3.5.0.1-1.el7 base 13 k python-ipaddress noarch 1.0.16-2.el7 base 34 k python-pytoml noarch 0.1.14-1.git7dea353.el7 extras 18 k python-setuptools noarch 0.9.8-7.el7 base 397 k setools-libs x86_64 3.3.8-4.el7 base 620 k socat x86_64 1.7.3.2-2.el7 base 290 k subscription-manager-rhsm-certificates x86_64 1.24.13-3.el7.centos updates 228 k yajl x86_64 2.0.4-4.el7 base 39 k Updating for dependencies: audit x86_64 2.8.5-4.el7 base 256 k audit-libs x86_64 2.8.5-4.el7 base 102 k libselinux x86_64 2.5-14.1.el7 base 162 k libselinux-python x86_64 2.5-14.1.el7 base 235 k libselinux-utils x86_64 2.5-14.1.el7 base 151 k libsemanage x86_64 2.5-14.el7 base 151 k libsepol x86_64 2.5-10.el7 base 297 k policycoreutils x86_64 2.5-33.el7 base 916 k selinux-policy noarch 3.13.1-252.el7.1 updates 492 k selinux-policy-targeted noarch 3.13.1-252.el7.1 updates 7.0 M Transaction Summary Install 2 Packages (+35 Dependent packages) Upgrade ( 10 Dependent packages) Total size: 93 M Downloading packages: warning: /var/cache/yum/x86_64/7/kubernetes/packages/8a0e2b605c7a616d7cb72c25c9058b2327e41d869046c7c6cb3930f10a3dc012-kubelet-1.16.3-0.x86_64.rpm: Header V4 RSA/SHA512 Signature, key ID 3e1ba8d5: NOKEY Retrieving key from https://packages.cloud.google.com/yum/doc/yum-key.gpg Importing GPG key 0xA7317B0F: Userid : "Google Cloud Packages Automatic Signing Key gc-team@google.com" Fingerprint: d0bc 747f d8ca f711 7500 d6fa 3746 c208 a731 7b0f From : https://packages.cloud.google.com/yum/doc/yum-key.gpg Retrieving key from https://packages.cloud.google.com/yum/doc/rpm-package-key.gpg Importing GPG key 0x3E1BA8D5: Userid : "Google Cloud Packages RPM Signing Key gc-team@google.com" Fingerprint: 3749 e1ba 95a8 6ce0 5454 6ed2 f09c 394c 3e1b a8d5 From : https://packages.cloud.google.com/yum/doc/rpm-package-key.gpg Running transaction check Running transaction test Transaction test succeeded Running transaction Updating : libsepol-2.5-10.el7.x86_64 1/57 Updating : libselinux-2.5-14.1.el7.x86_64 2/57 Updating : audit-libs-2.8.5-4.el7.x86_64 3/57 Updating : libsemanage-2.5-14.el7.x86_64 4/57 Updating : libselinux-utils-2.5-14.1.el7.x86_64 5/57 Updating : policycoreutils-2.5-33.el7.x86_64 6/57 Updating : selinux-policy-3.13.1-252.el7.1.noarch 7/57 Installing : yajl-2.0.4-4.el7.x86_64 8/57 Installing : 2:oci-umount-2.5-3.el7.x86_64 9/57 Installing : 1:oci-systemd-hook-0.2.0-1.git05e6923.el7_6.x86_64 10/57 Updating : selinux-policy-targeted-3.13.1-252.el7.1.noarch 11/57 Installing : libsemanage-python-2.5-14.el7.x86_64 12/57 Installing : audit-libs-python-2.8.5-4.el7.x86_64 13/57 Installing : setools-libs-3.3.8-4.el7.x86_64 14/57 Updating : libselinux-python-2.5-14.1.el7.x86_64 15/57 Installing : libcgroup-0.41-21.el7.x86_64 16/57 Installing : libnetfilter_cttimeout-1.0.0-6.el7_7.1.x86_64 17/57 Installing : subscription-manager-rhsm-certificates-1.24.13-3.el7.centos.x86_64 18/57 Installing : socat-1.7.3.2-2.el7.x86_64 19/57 Installing : python-ipaddress-1.0.16-2.el7.noarch 20/57 Installing : cri-tools-1.13.0-0.x86_64 21/57 Installing : libyaml-0.1.4-11.el7_0.x86_64 22/57 Installing : PyYAML-3.10-11.el7.x86_64 23/57 Installing : python-backports-1.0-8.el7.x86_64 24/57 Installing : python-backports-ssl_match_hostname-3.5.0.1-1.el7.noarch 25/57 Installing : python-setuptools-0.9.8-7.el7.noarch 26/57 Installing : 1:oci-register-machine-0-6.git2b44233.el7.x86_64 27/57 Installing : python-pytoml-0.1.14-1.git7dea353.el7.noarch 28/57 Installing : 1:atomic-registries-1.22.1-29.gitb507039.el7.x86_64 29/57 Installing : 1:containers-common-0.1.37-3.el7.centos.x86_64 30/57 Installing : python-IPy-0.75-6.el7.noarch 31/57 Installing : checkpolicy-2.5-8.el7.x86_64 32/57 Installing : policycoreutils-python-2.5-33.el7.x86_64 33/57 Installing : 2:container-selinux-2.107-3.el7.noarch 34/57 Installing : libnetfilter_cthelper-1.0.0-10.el7_7.1.x86_64 35/57 Installing : kubectl-1.16.3-0.x86_64 36/57 Installing : container-storage-setup-0.11.0-2.git5eaf76c.el7.noarch 37/57 Installing : 2:docker-common-1.13.1-103.git7f2769b.el7.centos.x86_64 38/57 Installing : 2:docker-client-1.13.1-103.git7f2769b.el7.centos.x86_64 39/57 Installing : libseccomp-2.3.1-3.el7.x86_64 40/57 Installing : libnetfilter_queue-1.0.2-2.el7_2.x86_64 41/57 Installing : conntrack-tools-1.4.4-5.el7_7.2.x86_64 42/57 Installing : kubernetes-cni-0.7.5-0.x86_64 43/57 Installing : kubelet-1.16.3-0.x86_64 44/57 Installing : kubeadm-1.16.3-0.x86_64 45/57 Installing : 2:docker-1.13.1-103.git7f2769b.el7.centos.x86_64 46/57 Updating : audit-2.8.5-4.el7.x86_64 47/57 Cleanup : selinux-policy-targeted-3.13.1-192.el7.noarch 48/57 Cleanup : selinux-policy-3.13.1-192.el7.noarch 49/57 Cleanup : policycoreutils-2.5-22.el7.x86_64 50/57 Cleanup : libsemanage-2.5-11.el7.x86_64 51/57 Cleanup : libselinux-utils-2.5-12.el7.x86_64 52/57 Cleanup : libselinux-python-2.5-12.el7.x86_64 53/57 Cleanup : libselinux-2.5-12.el7.x86_64 54/57 Cleanup : audit-2.8.1-3.el7.x86_64 55/57 Cleanup : audit-libs-2.8.1-3.el7.x86_64 56/57 Cleanup : libsepol-2.5-8.1.el7.x86_64 57/57 Verifying : 2:docker-common-1.13.1-103.git7f2769b.el7.centos.x86_64 1/57 Verifying : 2:docker-1.13.1-103.git7f2769b.el7.centos.x86_64 2/57 Verifying : python-backports-ssl_match_hostname-3.5.0.1-1.el7.noarch 3/57 Verifying : kubelet-1.16.3-0.x86_64 4/57 Verifying : libnetfilter_queue-1.0.2-2.el7_2.x86_64 5/57 Verifying : setools-libs-3.3.8-4.el7.x86_64 6/57 Verifying : 2:container-selinux-2.107-3.el7.noarch 7/57 Verifying : libseccomp-2.3.1-3.el7.x86_64 8/57 Verifying : container-storage-setup-0.11.0-2.git5eaf76c.el7.noarch 9/57 Verifying : kubectl-1.16.3-0.x86_64 10/57 Verifying : 1:atomic-registries-1.22.1-29.gitb507039.el7.x86_64 11/57 Verifying : python-setuptools-0.9.8-7.el7.noarch 12/57 Verifying : audit-libs-python-2.8.5-4.el7.x86_64 13/57 Verifying : libnetfilter_cthelper-1.0.0-10.el7_7.1.x86_64 14/57 Verifying : checkpolicy-2.5-8.el7.x86_64 15/57 Verifying : python-IPy-0.75-6.el7.noarch 16/57 Verifying : audit-libs-2.8.5-4.el7.x86_64 17/57 Verifying : 1:containers-common-0.1.37-3.el7.centos.x86_64 18/57 Verifying : 2:oci-umount-2.5-3.el7.x86_64 19/57 Verifying : python-pytoml-0.1.14-1.git7dea353.el7.noarch 20/57 Verifying : kubeadm-1.16.3-0.x86_64 21/57 Verifying : policycoreutils-python-2.5-33.el7.x86_64 22/57 Verifying : audit-2.8.5-4.el7.x86_64 23/57 Verifying : libsemanage-2.5-14.el7.x86_64 24/57 Verifying : libsemanage-python-2.5-14.el7.x86_64 25/57 Verifying : 1:oci-systemd-hook-0.2.0-1.git05e6923.el7_6.x86_64 26/57 Verifying : selinux-policy-targeted-3.13.1-252.el7.1.noarch 27/57 Verifying : 2:docker-client-1.13.1-103.git7f2769b.el7.centos.x86_64 28/57 Verifying : selinux-policy-3.13.1-252.el7.1.noarch 29/57 Verifying : libsepol-2.5-10.el7.x86_64 30/57 Verifying : 1:oci-register-machine-0-6.git2b44233.el7.x86_64 31/57 Verifying : python-backports-1.0-8.el7.x86_64 32/57 Verifying : yajl-2.0.4-4.el7.x86_64 33/57 Verifying : policycoreutils-2.5-33.el7.x86_64 34/57 Verifying : libselinux-python-2.5-14.1.el7.x86_64 35/57 Verifying : libyaml-0.1.4-11.el7_0.x86_64 36/57 Verifying : conntrack-tools-1.4.4-5.el7_7.2.x86_64 37/57 Verifying : libselinux-utils-2.5-14.1.el7.x86_64 38/57 Verifying : cri-tools-1.13.0-0.x86_64 39/57 Verifying : python-ipaddress-1.0.16-2.el7.noarch 40/57 Verifying : PyYAML-3.10-11.el7.x86_64 41/57 Verifying : kubernetes-cni-0.7.5-0.x86_64 42/57 Verifying : socat-1.7.3.2-2.el7.x86_64 43/57 Verifying : libselinux-2.5-14.1.el7.x86_64 44/57 Verifying : subscription-manager-rhsm-certificates-1.24.13-3.el7.centos.x86_64 45/57 Verifying : libnetfilter_cttimeout-1.0.0-6.el7_7.1.x86_64 46/57 Verifying : libcgroup-0.41-21.el7.x86_64 47/57 Verifying : libsemanage-2.5-11.el7.x86_64 48/57 Verifying : libselinux-utils-2.5-12.el7.x86_64 49/57 Verifying : policycoreutils-2.5-22.el7.x86_64 50/57 Verifying : libselinux-python-2.5-12.el7.x86_64 51/57 Verifying : audit-2.8.1-3.el7.x86_64 52/57 Verifying : selinux-policy-targeted-3.13.1-192.el7.noarch 53/57 Verifying : audit-libs-2.8.1-3.el7.x86_64 54/57 Verifying : libsepol-2.5-8.1.el7.x86_64 55/57 Verifying : selinux-policy-3.13.1-192.el7.noarch 56/57 Verifying : libselinux-2.5-12.el7.x86_64 57/57 Installed: docker.x86_64 2:1.13.1-103.git7f2769b.el7.centos kubeadm.x86_64 0:1.16.3-0 Dependency Installed: PyYAML.x86_64 0:3.10-11.el7 atomic-registries.x86_64 1:1.22.1-29.gitb507039.el7 audit-libs-python.x86_64 0:2.8.5-4.el7 checkpolicy.x86_64 0:2.5-8.el7 conntrack-tools.x86_64 0:1.4.4-5.el7_7.2 container-selinux.noarch 2:2.107-3.el7 container-storage-setup.noarch 0:0.11.0-2.git5eaf76c.el7 containers-common.x86_64 1:0.1.37-3.el7.centos cri-tools.x86_64 0:1.13.0-0 docker-client.x86_64 2:1.13.1-103.git7f2769b.el7.centos docker-common.x86_64 2:1.13.1-103.git7f2769b.el7.centos kubectl.x86_64 0:1.16.3-0 kubelet.x86_64 0:1.16.3-0 kubernetes-cni.x86_64 0:0.7.5-0 libcgroup.x86_64 0:0.41-21.el7 libnetfilter_cthelper.x86_64 0:1.0.0-10.el7_7.1 libnetfilter_cttimeout.x86_64 0:1.0.0-6.el7_7.1 libnetfilter_queue.x86_64 0:1.0.2-2.el7_2 libseccomp.x86_64 0:2.3.1-3.el7 libsemanage-python.x86_64 0:2.5-14.el7 libyaml.x86_64 0:0.1.4-11.el7_0 oci-register-machine.x86_64 1:0-6.git2b44233.el7 oci-systemd-hook.x86_64 1:0.2.0-1.git05e6923.el7_6 oci-umount.x86_64 2:2.5-3.el7 policycoreutils-python.x86_64 0:2.5-33.el7 python-IPy.noarch 0:0.75-6.el7 python-backports.x86_64 0:1.0-8.el7 python-backports-ssl_match_hostname.noarch 0:3.5.0.1-1.el7 python-ipaddress.noarch 0:1.0.16-2.el7 python-pytoml.noarch 0:0.1.14-1.git7dea353.el7 python-setuptools.noarch 0:0.9.8-7.el7 setools-libs.x86_64 0:3.3.8-4.el7 socat.x86_64 0:1.7.3.2-2.el7 subscription-manager-rhsm-certificates.x86_64 0:1.24.13-3.el7.centos yajl.x86_64 0:2.0.4-4.el7 Dependency Updated: audit.x86_64 0:2.8.5-4.el7 audit-libs.x86_64 0:2.8.5-4.el7 libselinux.x86_64 0:2.5-14.1.el7 libselinux-python.x86_64 0:2.5-14.1.el7 libselinux-utils.x86_64 0:2.5-14.1.el7 libsemanage.x86_64 0:2.5-14.el7 libsepol.x86_64 0:2.5-10.el7 policycoreutils.x86_64 0:2.5-33.el7 selinux-policy.noarch 0:3.13.1-252.el7.1 selinux-policy-targeted.noarch 0:3.13.1-252.el7.1 Complete! [root@urclouds-master ~]#
You can see we have successfully installed Kubeadm and Docker packages.
Now we need to be enable and start these services.
[root@urclouds-master ~]# systemctl restart docker && systemctl enable docker Created symlink from /etc/systemd/system/multi-user.target.wants/docker.service to /usr/lib/systemd/system/docker.service. [root@urclouds-master ~]# systemctl restart kubelet && systemctl enable kubelet Created symlink from /etc/systemd/system/multi-user.target.wants/kubelet.service to /usr/lib/systemd/system/kubelet.service. [root@urclouds-master ~]#
If you getting these error: –
[root@urclouds-master ~]# kubeadm init
[init] Using Kubernetes version: v1.16.3
[preflight] Running pre-flight checks
[WARNING Firewalld]: firewalld is active, please ensure ports [6443 10250] are open or your cluster may not function correctly
error execution phase preflight: [preflight] Some fatal errors occurred:
[ERROR NumCPU]: the number of available CPUs 1 is less than the required 2
[ERROR Swap]: running with swap on is not supported. Please disable swap
[preflroot@urclouds-master ~]#
We have already open all related to port so we can ingnore ports related warning but we need to be fixe CPU error and SWAP error. I have increased the CPU from 1 to 2 in our master node VM.
We have also disabled swap partition to comments swap partition in /etc/fstab file. After that VM has been rebooted. Like below: –
[root@urclouds-master ~]# vi /etc/fstab [root@urclouds-master ~]# cat /etc/fstab |grep swap /dev/mapper/centos-swap swap swap defaults 0 0 [root@urclouds-master ~]# reboot
After that, these error has been fixed in our master node.
Initialize Kubernetes Master node with kubeadm init
We have to run the below command to initialize and setup kubernetes master node.
[root@urclouds-master ~]# kubeadm init
[init] Using Kubernetes version: v1.16.3
[preflight] Running pre-flight checks
[WARNING Firewalld]: firewalld is active, please ensure ports [6443 10250] are open or your cluster may not function correctly
[preflight] Pulling images required for setting up a Kubernetes cluster
[preflight] This might take a minute or two, depending on the speed of your internet connection
[preflight] You can also perform this action in beforehand using 'kubeadm config images pull'
[kubelet-start] Writing kubelet environment file with flags to file "/var/lib/kubelet/kubeadm-flags.env"
[kubelet-start] Writing kubelet configuration to file "/var/lib/kubelet/config.yaml"
[kubelet-start] Activating the kubelet service
[certs] Using certificateDir folder "/etc/kubernetes/pki"
[certs] Generating "ca" certificate and key
[certs] Generating "apiserver" certificate and key
[certs] apiserver serving cert is signed for DNS names [urclouds-master kubernetes kubernetes.default kubernetes.default.svc kubernetes.default.svc.cluster.local] and IPs [10.96.0.1 192.168.43.132]
[certs] Generating "apiserver-kubelet-client" certificate and key
[certs] Generating "front-proxy-ca" certificate and key
[certs] Generating "front-proxy-client" certificate and key
[certs] Generating "etcd/ca" certificate and key
[certs] Generating "etcd/server" certificate and key
[certs] etcd/server serving cert is signed for DNS names [urclouds-master localhost] and IPs [192.168.43.132 127.0.0.1 ::1]
[certs] Generating "etcd/peer" certificate and key
[certs] etcd/peer serving cert is signed for DNS names [urclouds-master localhost] and IPs [192.168.43.132 127.0.0.1 ::1]
[certs] Generating "etcd/healthcheck-client" certificate and key
[certs] Generating "apiserver-etcd-client" certificate and key
[certs] Generating "sa" key and public key
[kubeconfig] Using kubeconfig folder "/etc/kubernetes"
[kubeconfig] Writing "admin.conf" kubeconfig file
[kubeconfig] Writing "kubelet.conf" kubeconfig file
[kubeconfig] Writing "controller-manager.conf" kubeconfig file
[kubeconfig] Writing "scheduler.conf" kubeconfig file
[control-plane] Using manifest folder "/etc/kubernetes/manifests"
[control-plane] Creating static Pod manifest for "kube-apiserver"
[control-plane] Creating static Pod manifest for "kube-controller-manager"
[control-plane] Creating static Pod manifest for "kube-scheduler"
[etcd] Creating static Pod manifest for local etcd in "/etc/kubernetes/manifests"
[wait-control-plane] Waiting for the kubelet to boot up the control plane as static Pods from directory "/etc/kubernetes/manifests". This can take up to 4m0s
[kubelet-check] Initial timeout of 40s passed.
[apiclient] All control plane components are healthy after 40.005169 seconds
[upload-config] Storing the configuration used in ConfigMap "kubeadm-config" in the "kube-system" Namespace
[kubelet] Creating a ConfigMap "kubelet-config-1.16" in namespace kube-system with the configuration for the kubelets in the cluster
[upload-certs] Skipping phase. Please see --upload-certs
[mark-control-plane] Marking the node urclouds-master as control-plane by adding the label "node-role.kubernetes.io/master=''"
[mark-control-plane] Marking the node urclouds-master as control-plane by adding the taints [node-role.kubernetes.io/master:NoSchedule]
[bootstrap-token] Using token: eoyfvl.6n137zip3d2k7az7
[bootstrap-token] Configuring bootstrap tokens, cluster-info ConfigMap, RBAC Roles
[bootstrap-token] configured RBAC rules to allow Node Bootstrap tokens to post CSRs in order for nodes to get long term certificate credentials
[bootstrap-token] configured RBAC rules to allow the csrapprover controller automatically approve CSRs from a Node Bootstrap Token
[bootstrap-token] configured RBAC rules to allow certificate rotation for all node client certificates in the cluster
[bootstrap-token] Creating the "cluster-info" ConfigMap in the "kube-public" namespace
[addons] Applied essential addon: CoreDNS
[addons] Applied essential addon: kube-proxy
Your Kubernetes control-plane has initialized successfully!
To start using your cluster, you need to run the following as a regular user:
mkdir -p $HOME/.kube
sudo cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
sudo chown $(id -u):$(id -g) $HOME/.kube/config
You should now deploy a pod network to the cluster.
Run "kubectl apply -f [podnetwork].yaml" with one of the options listed at:
https://kubernetes.io/docs/concepts/cluster-administration/addons/
Then you can join any number of worker nodes by running the following on each as root:
kubeadm join 192.168.43.132:6443 --token eoyfvl.6n137zip3d2k7az7 \
--discovery-token-ca-cert-hash sha256:bd43903f2786f3b0729859fb31416b539ef4e631a4f12559600785c9001de548
[root@urclouds-master ~]#
We can see in the above output that kubernetes master node has been successfully initialized. Now we must execute the below commands to use the cluster as root user.
[root@urclouds-master ~]# mkdir -p $HOME/.kube [root@urclouds-master ~]# cp -i /etc/kubernetes/admin.conf $HOME/.kube/config [root@urclouds-master ~]# chown $(id -u):$(id -g) $HOME/.kube/config [root@urclouds-master ~]#
Run below commands to get status of cluster and pods.
[root@urclouds-master ~]# kubectl get nodes NAME STATUS ROLES AGE VERSION urclouds-master NotReady master 12m v1.16.3 [root@urclouds-master ~]# [root@urclouds-master ~]# kubectl get pods --all-namespaces NAMESPACE NAME READY STATUS RESTARTS AGE kube-system coredns-5644d7b6d9-gdrdg 0/1 Pending 0 13m kube-system coredns-5644d7b6d9-lpj4l 0/1 Pending 0 13m kube-system etcd-urclouds-master 1/1 Running 0 12m kube-system kube-apiserver-urclouds-master 1/1 Running 0 12m kube-system kube-controller-manager-urclouds-master 1/1 Running 0 12m kube-system kube-proxy-nsjmf 1/1 Running 0 13m kube-system kube-scheduler-urclouds-master 1/1 Running 0 12m [root@urclouds-master ~]#
Deploy pod network to the cluster
We need to be deployed the pod network so that containers of different host can communicated with each other. POD network is the overlay network between the worker nodes. Run the below command to deploy network.
[root@urclouds-master ~]# export kubever=$(kubectl version | base64 | tr -d '\n') [root@urclouds-master ~]# kubectl apply -f "https://cloud.weave.works/k8s/net?k8s-version=$kubever" serviceaccount/weave-net created clusterrole.rbac.authorization.k8s.io/weave-net created clusterrolebinding.rbac.authorization.k8s.io/weave-net created role.rbac.authorization.k8s.io/weave-net created rolebinding.rbac.authorization.k8s.io/weave-net created daemonset.apps/weave-net created [root@urclouds-master ~]#
Run the below command to verify the status
[root@urclouds-master ~]# kubectl get pods --all-namespaces NAMESPACE NAME READY STATUS RESTARTS AGE kube-system coredns-5644d7b6d9-gdrdg 1/1 Running 0 18m kube-system coredns-5644d7b6d9-lpj4l 1/1 Running 0 18m kube-system etcd-urclouds-master 1/1 Running 0 17m kube-system kube-apiserver-urclouds-master 1/1 Running 0 17m kube-system kube-controller-manager-urclouds-master 1/1 Running 0 17m kube-system kube-proxy-nsjmf 1/1 Running 0 18m kube-system kube-scheduler-urclouds-master 1/1 Running 0 17m kube-system weave-net-gs9lm 2/2 Running 0 69s [root@urclouds-master ~]#
You can see here, we have successfully install kubernetes on master node.
Now we will see worker node installation step by steps.
First off all we have to set hostname and disable SELinux with below commands:-
[root@localhost ~]# hostnamectl set-hostname urclouds-node1 [root@localhost ~]# exec bash [root@urclouds-node1 ~]# setenforce 0 [root@urclouds-node1 ~]# sed -i --follow-symlinks 's/SELINUX=enforcing/SELINUX=disabled/g' /etc/sysconfig/selinux [root@urclouds-node1 ~]# firewall-cmd --permanent --add-port=10250/tcp success [root@urclouds-node1 ~]# firewall-cmd --permanent --add-port=10255/tcp success [root@urclouds-node1 ~]# firewall-cmd --permanent --add-port=30000-32767/tcp success [root@urclouds-node1 ~]# firewall-cmd --permanent --add-port=6783/tcp success [root@urclouds-node1 ~]# firewall-cmd --reload success [root@urclouds-node1 ~]# [root@urclouds-node1 ~]# modprobe br_netfilter [root@urclouds-node1 ~]# echo '1' > /proc/sys/net/bridge/bridge-nf-call-iptables [root@urclouds-node1 ~]#
After that we need to configure Kubernetes Repositories on both worker nodes as like below: –
[root@urclouds-node1 ~]# vi /etc/yum.repos.d/kubernetes.repo [root@urclouds-node1 ~]# cat /etc/yum.repos.d/kubernetes.repo [kubernetes] name=Kubernetes baseurl=https://packages.cloud.google.com/yum/repos/kubernetes-el7-x86_64 enabled=1 gpgcheck=1 repo_gpgcheck=1 gpgkey=https://packages.cloud.google.com/yum/doc/yum-key.gpg https://packages.cloud.google.com/yum/doc/rpm-package-key.gpg [root@urclouds-node1 ~]#
Install kubeadm package and docker package on both nodes
[root@urclouds-node1 ~]# yum install kubeadm docker -y [root@urclouds-node2 ~]# yum install kubeadm docker -y
After packages installation we can start and enable docker and kubelet service as below commands: –
[root@urclouds-node1 ~]# systemctl restart docker && systemctl enable docker Created symlink from /etc/systemd/system/multi-user.target.wants/docker.service to /usr/lib/systemd/system/docker.service. [root@urclouds-node1 ~]# [root@urclouds-node1 ~]# systemctl restart kubelet && systemctl enable kubele Created symlink from /etc/systemd/system/multi-user.target.wants/kubelet.service to /usr/lib/systemd/system/kubelet.service. [root@urclouds-node1 ~]#
Now we can join worker nodes to master node with below commands: –
[root@urclouds-node1 ~]# kubeadm join 192.168.43.132:6443 --token eoyfvl.6n137zip3d2k7az7 --discovery-token-ca-cert-hash sha256:bd43903f2786f3b0729859fb31416b539ef4e631a4f12559600785c9001de548 [preflight] Running pre-flight checks [preflight] Reading configuration from the cluster… [preflight] FYI: You can look at this config file with 'kubectl -n kube-system get cm kubeadm-config -oyaml' [kubelet-start] Downloading configuration for the kubelet from the "kubelet-config-1.16" ConfigMap in the kube-system namespace [kubelet-start] Writing kubelet configuration to file "/var/lib/kubelet/config.yaml" [kubelet-start] Writing kubelet environment file with flags to file "/var/lib/kubelet/kubeadm-flags.env" [kubelet-start] Activating the kubelet service [kubelet-start] Waiting for the kubelet to perform the TLS Bootstrap… This node has joined the cluster: Certificate signing request was sent to apiserver and a response was received. The Kubelet was informed of the new secure connection details. Run 'kubectl get nodes' on the control-plane to see this node join the cluster. [root@urclouds-node1 ~]#
You can see in above output we have susccessfully joined the work node in master node.
Now we can verify Nodes status from master node using kubectl command like below: –
[root@urclouds-master ~]# kubectl get nodes NAME STATUS ROLES AGE VERSION urclouds-master Ready master 107m v1.16.3 urclouds-node1 Ready 5m37s v1.16.3 [root@urclouds-master ~]#
In above output we can see our master node and worker node is ready.
So we can install multi worker node and we can join our all worker nodes to master nodes, and we can manage all container through master node.
That’s all in this tutorial we have seen how to install Kubernetes cluster on CentOS VM.
You can also click on this link to see how to install docker on CentOS 7.