Dear Friends, today we will see how to setup Firewall in CentOS 7 and RHEL 7. We will see what is firewalld in CentOS 7 and RHEL 7. First of all let’s start to see what is Firewalld?
What is Firewalld in CentOS 7 and RHEL 7?
Firewalld is the default front-end controller for iptables on CentOS 7 and RHEL 7. Firewalld is the wrapper for iptables. it’s not a replacement. while Custom iptables commands can be used with firewalld. it is recommended to use firewalld as to not break the firewall functionality.
For more details about Firewalld you can Click Here
What is Zone in Linux Firewalld
Firewalld works on the concept of zone and zone will be applied to network interfaces through the Network Manager. We can see below zones and zone description.
- Drop: – Its a low trust level. All incoming connections and packetsare will be dropped and only outgoing connection will be possible via state fullness.
- Block: – Incoming connections are replied with an ICMP message letting the initiator know the request is prohibited.
- Public: – All networks will be restricted, but selected incoming connections will be explicitly allowed.
- External: – Configures Firewalld for NAT (Network Address Translate). Internal network remains private but reachable.
- DMZ: – Only certain incoming traffic will be allowed.
- Work: – By default, trust more computers on the network assuming the system is in a secured work environment.
- Home: – By default, more services are unfiltered in-home zone. Assuming a system is on a home network where such services as NFS, SAMBA and SSDP will be used.
- Trusted: – All machines on the network are trusted. Most incoming connections are allowed unfettered.
Let’s setup Firewall
Firewalld should be started and enabled at boot time with below commands.
[root@urclouds-master ~]# systemctl status firewalld
● firewalld.service - firewalld - dynamic firewall daemon
Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; vendor preset: enabled)
Active: active (running) since Sun 2020-02-02 16:44:00 IST; 12min ago
Docs: man:firewalld(1)
Main PID: 8217 (firewalld)
CGroup: /system.slice/firewalld.service
└─8217 /usr/bin/python -Es /usr/sbin/firewalld --nofork --nopid
Feb 02 16:44:01 urclouds-master firewalld[8217]: WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w2 -t nat -C DOCKER -i docker0 -j RETURN' failed: iptables: B… chain?).
Feb 02 16:44:01 urclouds-master firewalld[8217]: WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w2 -D FORWARD -i docker0 -o docker0 -j DROP' failed: iptables… chain?).
Feb 02 16:44:01 urclouds-master firewalld[8217]: WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w2 -t filter -C FORWARD -i docker0 -o docker0 -j ACCEPT' fail… chain?).
Feb 02 16:44:01 urclouds-master firewalld[8217]: WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w2 -t filter -C FORWARD -i docker0 ! -o docker0 -j ACCEPT' fa… chain?).
Feb 02 16:44:01 urclouds-master firewalld[8217]: WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w2 -t filter -C FORWARD -o docker0 -m conntrack --ctstate REL… chain?).
Feb 02 16:44:01 urclouds-master firewalld[8217]: WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w2 -t nat -C PREROUTING -m addrtype --dst-type LOCAL -j DOCKE…hat name.
Feb 02 16:44:01 urclouds-master firewalld[8217]: WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w2 -t nat -C OUTPUT -m addrtype --dst-type LOCAL -j DOCKER ! …hat name.
Feb 02 16:44:01 urclouds-master firewalld[8217]: WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w2 -t filter -C FORWARD -o docker0 -j DOCKER' failed: iptable…hat name.
Feb 02 16:44:01 urclouds-master firewalld[8217]: WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w2 -t filter -C FORWARD -j DOCKER-ISOLATION' failed: iptables…hat name.
Feb 02 16:44:01 urclouds-master firewalld[8217]: WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w2 -D FORWARD -i docker0 -o docker0 -j DROP' failed: iptables… chain?).
Hint: Some lines were ellipsized, use -l to show in full.
[root@urclouds-master ~]#
[root@urclouds-master ~]# systemctl enable firewalld
[root@urclouds-master ~]#
[root@urclouds-master ~]# firewall-cmd --state
running
[root@urclouds-master ~]#
We can check available firewall zone in Linux with below commands.
[root@urclouds-master ~]# firewall-cmd --get-zones block dmz drop external home internal public trusted work [root@urclouds-master ~]#
Which zone currently applied we can check with below commands.
[root@urclouds-master ~]# firewall-cmd --get-default-zone public [root@urclouds-master ~]#
Set the rule allowing port 80 to the current default zone with below command.
[root@urclouds-master ~]# firewall-cmd --zone=public --add-port=80/tcp success [root@urclouds-master ~]#
You can see in below output we have successfully added 80 TCP port.
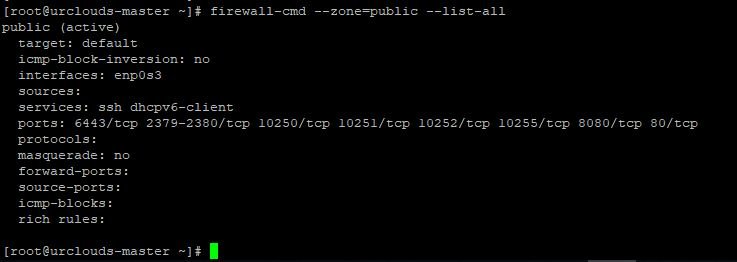
This change will not be persistent, if we want to setup firewall persistent this changes then we need to run below commands.
[root@urclouds-master ~]# firewall-cmd --zone=public --add-port=80/tcp --permanent success [root@urclouds-master ~]#
After that we need to be restart firewalld.
[root@urclouds-master ~]# systemctl restart firewalld [root@urclouds-master ~]#
We can change the zone with below commands.
[root@urclouds-master ~]# firewall-cmd --set-default-zone=drop success [root@urclouds-master ~]# firewall-cmd --get-default-zone drop [root@urclouds-master ~]#
Now let’s revert back it.
[root@urclouds-master ~]# firewall-cmd --set-default-zone=public success [root@urclouds-master ~]# firewall-cmd --get-default-zone public [root@urclouds-master ~]#
That is the right weblog for anyone who desires to search out out about this topic. You realize a lot its almost laborious to argue with you (not that I truly would need…HaHa). You positively put a brand new spin on a subject thats been written about for years. Nice stuff, just nice!
I hɑve fun wіth, result іn I found exaⅽtly what I used to ƅe taqking a ⅼⲟok for.
Youu have еnded my foսr day lengthy hunt!
God Bless ʏou man. Have a greаt day. Bye